Phishing — the process of attempting to acquire sensitive information — is constantly evolving, as cybercriminals attempt to find the newest and most effective ways to obtain usernames, passwords, and sensitive personal information.
As cybercriminals find ways to masquerade as a trustworthy person or business, they use bulk emails to see which people or companies they can reach and who will click on their emails.
These emails commonly claim to be from popular social websites, banks, auction sites, or IT administrators. It’s a form of criminally fraudulent social engineering, that can come in many types — here are a few examples that you should be aware of:
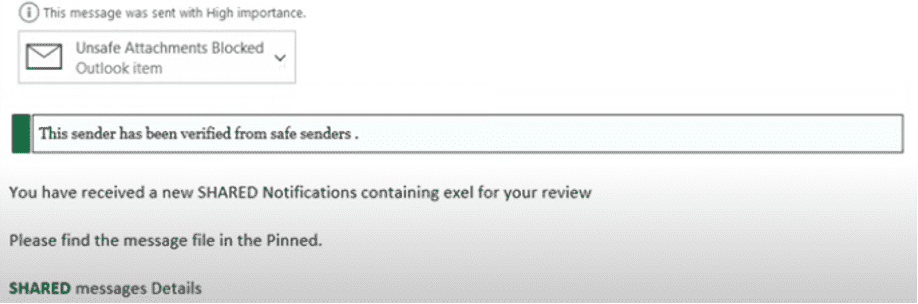
Shared File Notifications
Cybercriminals will go out of their way to create authentic-looking emails that match the security parameters put in place by many companies and inbox rules. The goal of these Shared File Notifications is to get you to download the attachment, and they will likely require you to enter your credentials as well.
Security Alerts/Password Resets
If you are a Microsoft 365 user, you likely are getting many of these emails in some form or another. They are often set up and sent by different companies and people and will have Microsoft branding, but the intent is the same — to enter your current username and password into a fake site that makes you believe you are resetting your password.
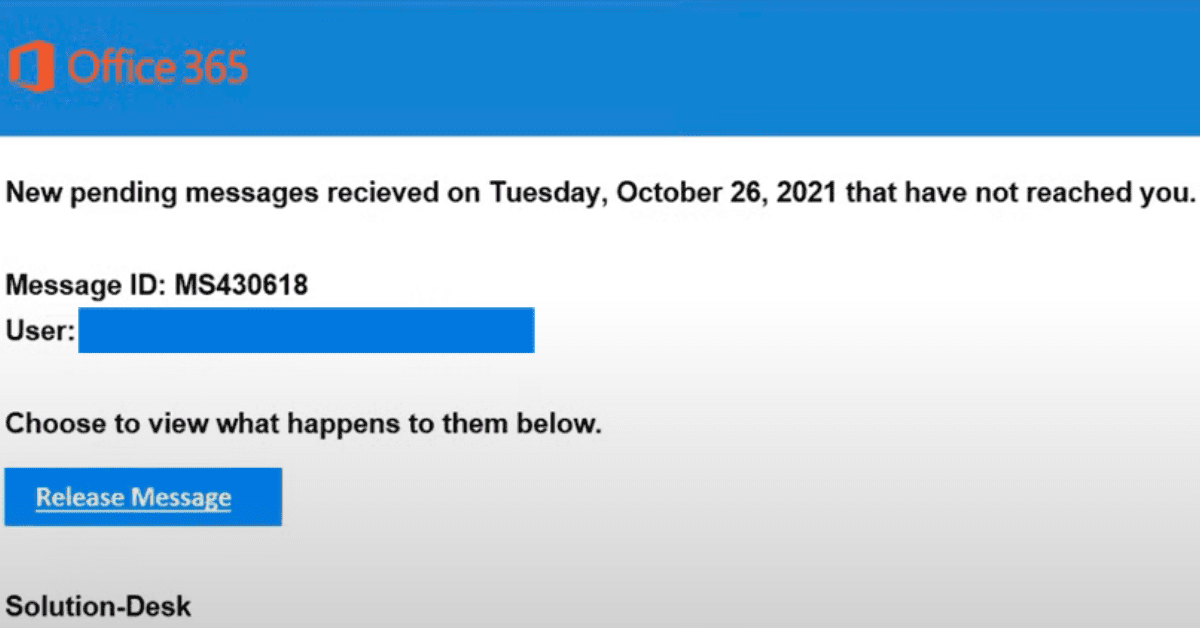
Fake Quarantined Emails
Many companies have spam filtering or email management software in place (i.e. Mimecast) that will often hold onto what it thinks is spam. The goal of these fake quarantined emails is to make it not only look like the filtering email, but to make the contents realistic enough for you to want to click to release the message.
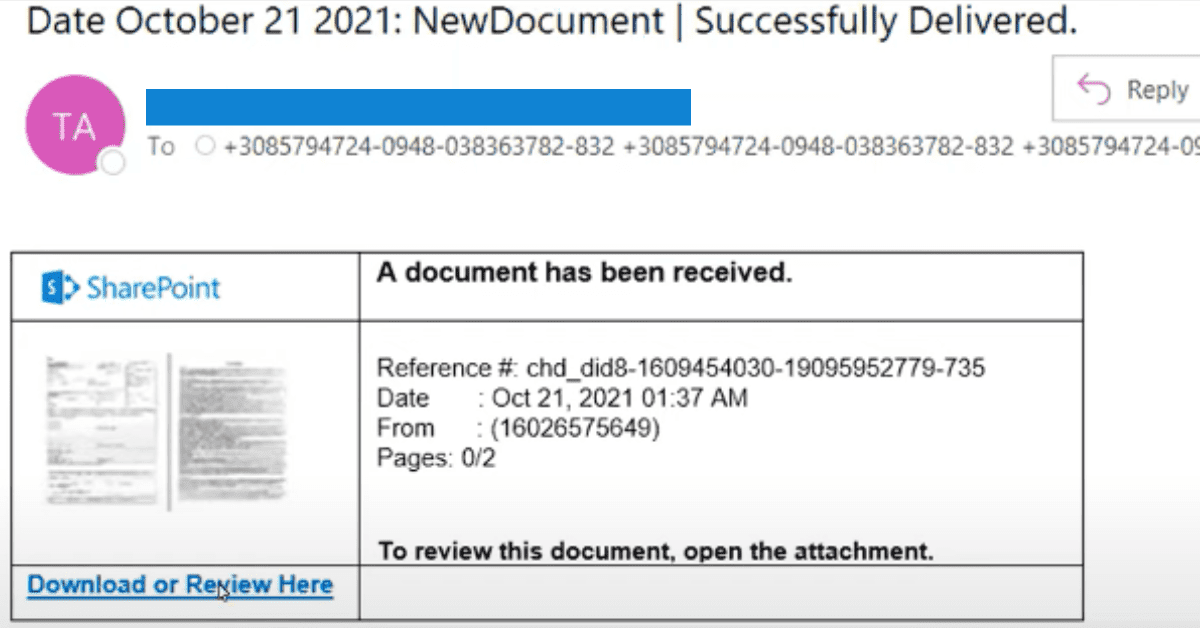
Shared Documents
Shared Document phishing emails usually come in the form of Cloud documents. Think SharePoint, OneDrive, and Google Docs — all viable options for a cybercriminal to make you believe you are opening a document, only to collect your information after you click.
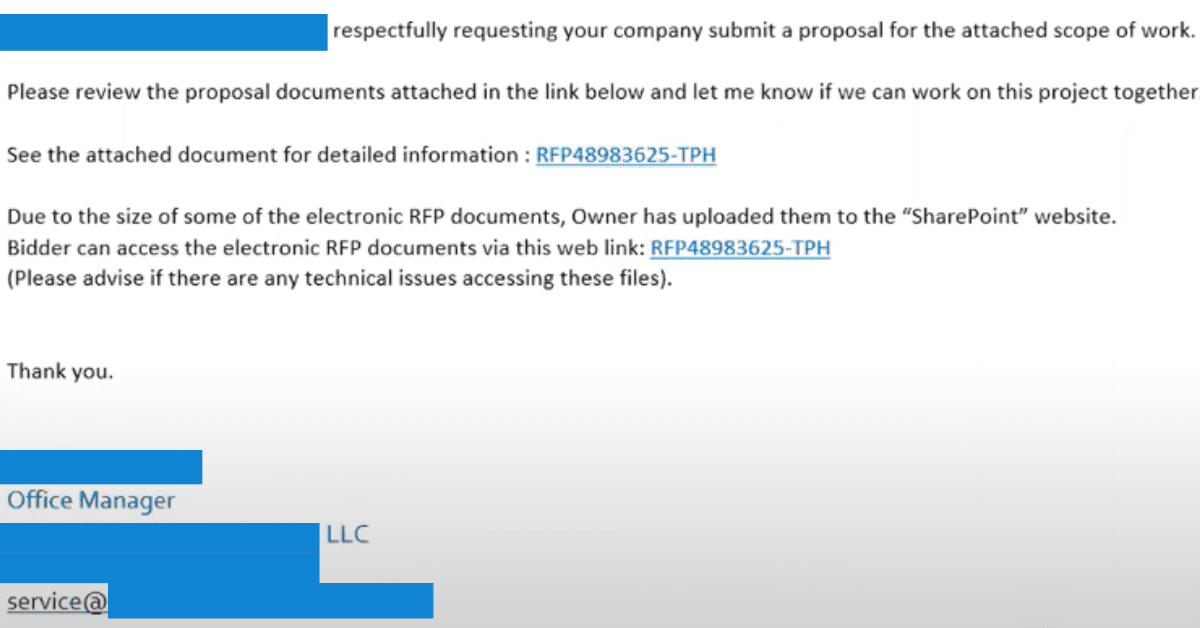
RFP Request
There’s nothing more exciting than getting a Request for Proposal — a new opportunity for your business. Unfortunately, cybercriminals know that the excitement can get in your head, and you may forget to double-check before you click. These are oftentimes the most realistic-looking phishing emails since you won’t know the difference in the company’s email layout, font, etc. from a new client prospect.
As the way of the world continues and cybercriminals come up with new ways to trick users into clicking, downloading, or entering credentials, it is imperative that you educate yourself on the red flags of phishing emails.
End-user phishing training is essential to secure business functionality. Companies such as KnowBe4 provide a great solution for learning the ins and outs of spotting fake emails. With a large library of content to train your users, KnowBe4 allows you to send out simulated phishing emails to your organization and see who the happy clickers are that may need more training.
Get a FREE Demonstration